Not every cyber incident starts with a sophisticated remote exploit. Sometimes it’s far simpler: a small, unauthorized device plugged into an Ethernet port creates a hidden path for communication, monitoring, or remote access.
Tools like “LAN Turtle” get attention because they represent a broader real-world risk: rogue network implants that enable covert channels. For medical device manufacturers, this matters across the product lifecycle—R&D labs, manufacturing test stations, service environments, and connected product ecosystems.
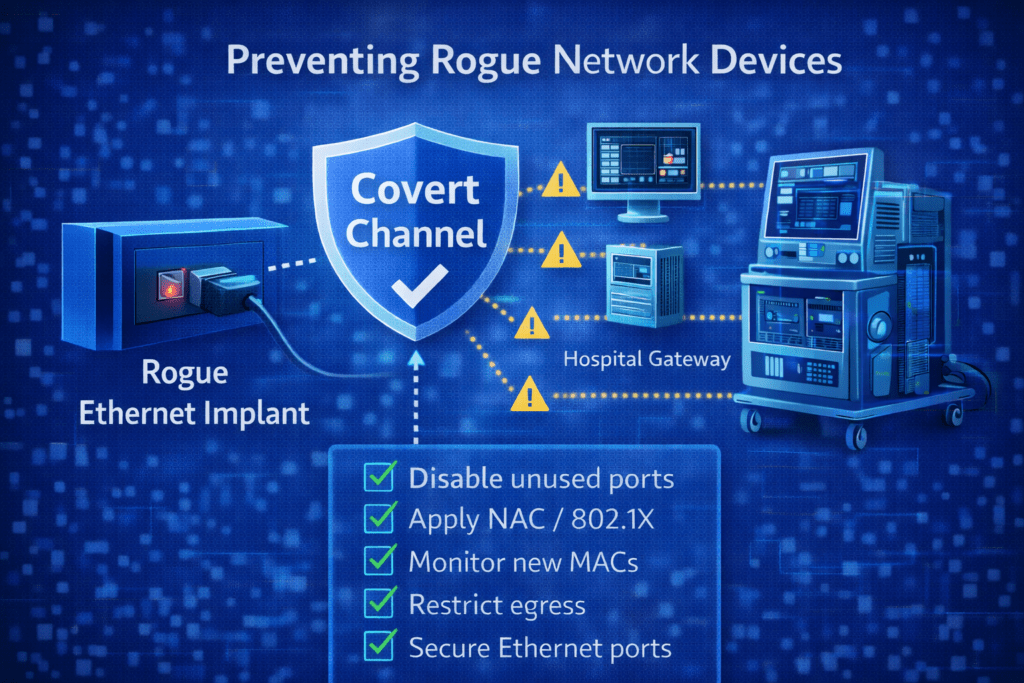
This article explains covert channels in plain language, why they matter in MedTech, and what you can do to prevent and detect them—without turning this into a “how-to” for misuse.
Note: Everything below is written from a defensive perspective for authorized environments only.
90-Day Quick Wins (A Practical Checklist)
If you want fast progress without boiling the ocean, start here:
- Disable unused switch ports in labs, manufacturing, and shared areas (and document ownership).
- Alert on new MAC addresses in sensitive VLANs (test benches, build systems, provisioning networks).
- Pilot NAC/802.1X on one segment first (e.g., a single lab or manufacturing line) before scaling.
- Segment by purpose: keep test/dev/service networks separate from corp/prod and restrict routes tightly.
- Restrict outbound traffic (egress) from non-user segments to only what’s required.
What Is a Covert Channel?
A covert channel is an unintended way for information to move in or out of an environment outside of approved communication paths. In network terms, it often looks like data leaving through “unexpected routes” or systems communicating in ways that aren’t documented or monitored.
Covert channels are dangerous because they can bypass normal visibility. If your monitoring and controls assume “only these systems talk to the internet,” covert channels challenge that assumption.
What Is a Rogue Network Implant?
A rogue network implant is a small device connected to a network (often via Ethernet) that introduces an unauthorized capability—like creating an extra network hop, enabling hidden communications, or bridging segments that should stay separate.
You don’t have to focus on a specific brand or gadget to manage the risk. The defensive goal is the same: prevent unknown devices from joining the network and detect them quickly if they do.
A Realistic MedTech Scenario (Why This Isn’t Hypothetical)
Here’s a pattern we see in the real world: a shared manufacturing test bench network has a small unmanaged switch tucked under a table “for convenience.” Multiple teams rotate hardware, contractors come and go, and the network port is always live. One day, a new device appears on the segment—no ticket, no change control, no owner. Even if the intent isn’t malicious, you’ve just lost confidence in what that network can reach, what it can exfiltrate, and how quickly you could detect a problem.
This is exactly where covert channels thrive: places with lots of access, weak ownership, and limited monitoring.
Why This Matters for Medical Device Manufacturers
MedTech environments are uniquely exposed to this class of risk because they often include:
- Shared lab networks with frequent device swaps and “temporary” setups
- Manufacturing test stations with long-lived network drops and mixed ownership
- Supplier and contract manufacturer access where boundaries can blur
- Service workflows involving laptops, diagnostic tools, and ad hoc connectivity
- Hybrid ecosystems (device + gateway + cloud + portal), where trust assumptions multiply
The impact can range from nuisance to serious:
- IP exposure (firmware, scripts, build artifacts, device logs)
- Unauthorized access pathways into internal networks or sensitive test environments
- Integrity risks (unauthorized changes to configs, provisioning data, or test results)
- Availability disruption in manufacturing, validation, or service environments
- Compliance headaches when you can’t confidently explain or bound what happened
Where These Risks Show Up in the Real World
In MedTech, rogue devices and covert channels most commonly appear in “in-between” places:
- an unattended Ethernet jack in a lab, staging area, or manufacturing floor
- a shared switch under a bench that no one “owns”
- a temporary network setup that became permanent
- a service environment where connectivity is frequently improvised
The takeaway is not paranoia—it’s ownership. If nobody owns a segment, nobody secures it.
How to Prevent Covert Channels from Rogue Ethernet Implants
If you only do one thing, do this: control who can connect. Most organizations get big wins from a handful of practical controls.
1) Use NAC / 802.1X for port-based access control
Network Access Control (often via 802.1X) helps ensure only authorized devices can connect to wired ports. It’s one of the strongest defenses against unknown devices quietly joining your network.
2) Enable switch port security (and shut down unused ports)
Basic switch hygiene makes a huge difference:
- disable unused ports
- limit the number of MAC addresses per port where appropriate
- alert when a new MAC address appears on sensitive segments
3) Segment networks by purpose (and keep test/dev away from sensitive systems)
Segmentation reduces blast radius. Even if an unauthorized device appears, it should land in a segment with limited access—not on a flat network where it can “see everything.”
4) Maintain an asset baseline for each environment
In labs and manufacturing, “unknown device detection” gets easier when you have a known-good baseline:
- expected MAC OUIs and device types
- expected DHCP patterns
- expected DNS domains and egress destinations
5) Monitor egress and enforce least privilege outbound access
Covert channels often rely on outbound connectivity. If everything can talk to anything, you’ll miss it. Egress filtering plus monitoring for unusual outbound patterns is a practical control.
6) Don’t ignore physical security
Physical access is a cybersecurity control. In many environments, small steps help:
- lock network closets and cabinets
- use port blockers where needed
- apply tamper-evident seals on sensitive enclosures
- limit access to unused drops and shared switches
Detection Signals: Rogue Device Detection in Labs and Manufacturing
You don’t need perfect tooling to catch most rogue implants—you need consistent attention to a few indicators:
- New or unexpected MAC addresses appearing on access ports (especially in labs/manufacturing)
- DHCP anomalies (new leases where you don’t expect them, unusual hostnames)
- DNS pattern changes (new domains, repeated queries, unexpected lookups)
- Unusual outbound connections from segments that normally shouldn’t have internet access
- Network topology surprises (a “device behind a device” appearance, or unexpected bridging)
- CAM table churn / ARP anomalies that don’t match normal behavior
For many teams, the most effective approach is simple: alert on “new device appears” events for sensitive segments and make sure someone is accountable for investigating.
What to Do If You Find One
- Contain: isolate the port/segment (don’t keep it connected “just to watch”).
- Preserve evidence: document switch port, timestamps, MAC address, DHCP lease, and traffic summaries.
- Triage impact: identify what the device could access from that location (segments, systems, credentials exposure).
- Eradicate and harden: remove the device and close the control gap (NAC, port shutdown, segmentation fixes).
- Verify: confirm no additional unauthorized devices exist and confirm alerts work going forward.
How to Make This Defensible in a Medical Device Cybersecurity Program
For regulated teams, it helps to connect these controls to your broader cybersecurity story:
- Design-time: define network assumptions and trust boundaries (threat modeling helps).
- Verification: validate segmentation and access controls in test and production-like environments.
- Operations/postmarket: document monitoring, incident handling, and recurring reviews.
In practice, this lets you answer: “How do we prevent unauthorized network devices from becoming hidden communication paths?” with specific, testable controls.
FAQs
What is a covert channel in network security?
A covert channel is an unintended or unauthorized way for data to move in or out of an environment outside approved communication paths—often reducing visibility and control.
Are rogue Ethernet implants a realistic concern in MedTech?
They can be, especially in labs, manufacturing floors, shared test benches, and service environments where physical access exists and ports are plentiful.
What’s the best first control to implement?
Port-based access control (NAC/802.1X) paired with disabling unused ports is usually the biggest win. Then add segmentation and alerting so “unknown device appears” becomes actionable.
Does segmentation still help if someone plugs in a rogue device?
Yes. Segmentation limits what that device can access and reduces blast radius. It turns a potential network-wide event into a bounded local issue.
External References (Trusted Resources)
- NIST SP 800-53 Rev. 5 (Security Controls: Access Control, Monitoring, Physical Security)
- NIST SP 800-207: Zero Trust Architecture (identity, device trust, segmentation)
- NIST SP 800-82: ICS Security (useful for manufacturing/test environments)
- CISA Zero Trust Maturity Model (roadmap concepts for devices and networks)
- CIS Critical Security Controls v8 (asset inventory, secure configuration, monitoring)
How Blue Goat Cyber Helps
If you want a realistic segmentation + NAC plan for labs, manufacturing, and service environments—and you need it documented in a way that’s defensible—Blue Goat Cyber can help you define trust boundaries, validate architectures, and align evidence with medical device cybersecurity expectations.
- Medical Device Threat Modeling
- Medical Device Vulnerability & Penetration Testing
- FDA Premarket Cybersecurity Services
- FDA Postmarket Cybersecurity Management
- Contact Blue Goat Cyber
Bottom line: covert channels aren’t a “cool hacker trick.” They’re a visibility problem. Control who can connect, segment by purpose, monitor for unknown devices, and treat physical access as part of your cybersecurity program.
