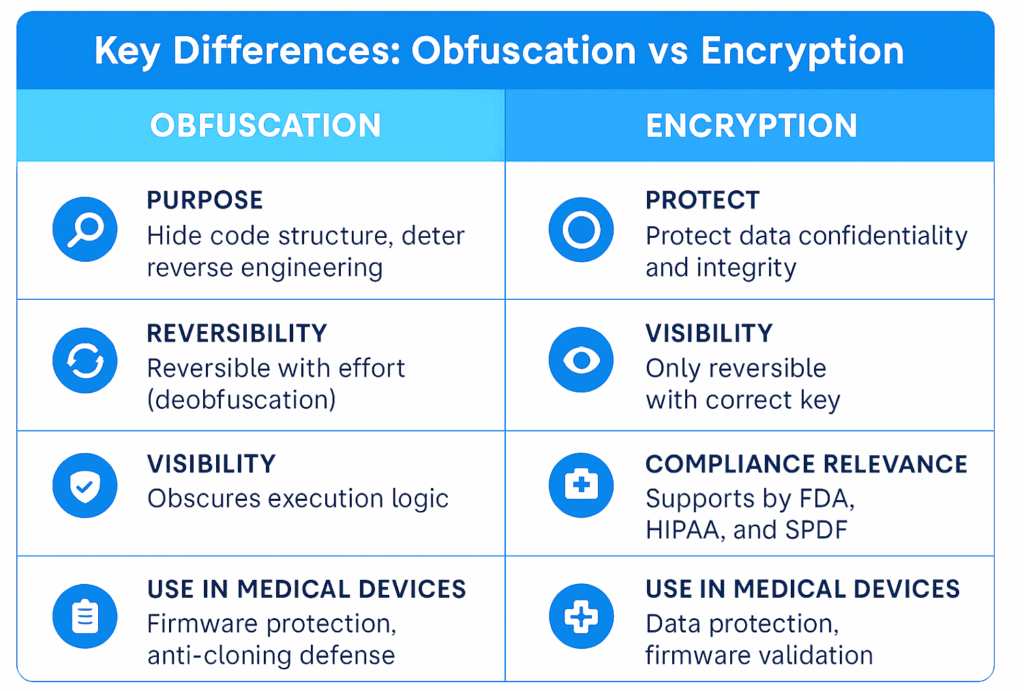
Encryption is often seen as a non-negotiable standard in medical device cybersecurity. But there’s another technique that’s just as important yet less understood: obfuscation.
Both encryption and obfuscation help protect devices, firmware, and patient data—but in very different ways. Knowing when and how to use each can help medical device manufacturers build stronger defenses, meet FDA cybersecurity guidance, and protect intellectual property (IP).
What Is Obfuscation?
Obfuscation is the practice of transforming code or data to make it difficult to interpret or reverse engineer, without altering its functionality. Unlike encryption, which is meant to secure data from unauthorized access, obfuscation is about hiding how code works.
🧩 Common Obfuscation Techniques:
- Renaming variables and functions (e.g.,
temp→x9fT) - Encrypting or compressing strings and resources
- Control flow flattening to obscure logic
- Packing or wrapping binaries with loaders
Real-World Example: A surgical robot manufacturer obfuscates motion-control algorithms in its firmware to protect IP from competitors and malicious modification.
What Is Encryption?
Encryption secures information by converting it into a coded format that can only be read with a cryptographic key. It is designed to protect the confidentiality and integrity of data at rest or in transit.
🔐 Encryption in Medical Devices:
- Data-in-transit: Secures telemetry from wearable monitors to cloud dashboards (e.g., TLS 1.3)
- Data-at-rest: Protects onboard logs, PHI, and configuration files (e.g., AES-256)
- Firmware authenticity: Digital signatures verify source and prevent tampering
Real-World Example: An insulin pump encrypts stored patient history and telemetry uploads to meet HIPAA and FDA cybersecurity expectations.
When to Use Each in Device Cybersecurity
✅ Use Obfuscation to:
- Protect sensitive algorithms or proprietary control code
- Deter reverse engineering from competitors or threat actors
- Slow attackers during firmware analysis or tampering
✅ Use Encryption to:
- Secure PHI and telemetry in compliance with HIPAA
- Authenticate firmware and OTA updates using signed hashes
- Secure communications between device, app, and cloud
Best Practice: Use both. Obfuscation adds a layer of defense-in-depth, while encryption enforces strict access control and compliance.
Implementation Checklist
Ensure you apply these practices in your Secure Product Development Framework (SPDF):
- ✅ Use FIPS 140-3 validated encryption libraries (e.g., OpenSSL, wolfCrypt)
- ✅ Obfuscate all proprietary logic or device command handlers
- ✅ Digitally sign firmware and validate via secure boot
- ✅ Incorporate static code analysis to verify obfuscation coverage
- ✅ Document both techniques in threat model and eSTAR submission
- ✅ Include obfuscation and encryption scenarios in penetration testing
Need help with this? Our SPDF consulting services are designed to help you integrate these controls and document them for the FDA.
Regulatory Context: What the FDA Expects
- The FDA’s 2025 Premarket Cybersecurity Guidance emphasizes:
- Data protection through encryption of PHI, logs, and telemetry
- Firmware integrity via cryptographic validation
- Clear documentation of risk mitigation strategies in your cybersecurity plan
- While obfuscation is not explicitly required, it demonstrates proactive risk management and enhances your defense against IP theft, firmware tampering, and device cloning.
FAQs
- Q: Is obfuscation a substitute for encryption?
A: No. Obfuscation obscures code but does not secure data. Encryption is needed for regulatory compliance and actual protection. - Q: Do open-source libraries support both?
A: Most major cryptographic libraries support encryption. Obfuscation is often implemented at build time using tools like LLVM Obfuscator or ProGuard. - Q: Will FDA reviewers ask about code obfuscation?
A: Not directly—but including it in your threat model or SPDF strengthens your submission, especially if reverse engineering is a concern.
Final Thoughts
- Encryption and obfuscation serve different, complementary roles in securing medical devices. Encryption protects data from unauthorized access and tampering—critical for FDA compliance. Obfuscation deters attackers from reverse engineering your firmware and helps guard intellectual property.
- Using both together ensures your devices are safer, more resilient, and regulatory-ready.
Partner With Blue Goat Cyber
We help medical device manufacturers design, implement, and validate both encryption frameworks and code obfuscation strategies. Our team specializes in FDA-ready security testing and documentation.
👉 Schedule your cybersecurity assessment and safeguard your firmware and data from the inside out.