Updated July 14, 2025
System on a Chip (SoC) technology powers nearly every modern connected medical device—from wearable monitors to surgical robots. These integrated microprocessors are efficient, compact, and capable. But they also introduce complex security risks that manufacturers must understand, document, and mitigate to meet FDA cybersecurity guidance.
In this article, we explore how SoC vulnerabilities have affected medical devices, which types of flaws pose the greatest threats, and what manufacturers must do to protect their products, patients, and market access.
What Are SoC Vulnerabilities?
An SoC combines a CPU, memory, wireless modules (like Bluetooth or Wi-Fi), and other peripheral components onto a single chip. This makes them ideal for low-power embedded systems like medical wearables, infusion pumps, and portable diagnostic equipment.
But the same integration that makes SoCs efficient also makes them a single point of failure.
If one component in the SoC—like the Bluetooth stack or TCP/IP firmware—is vulnerable, the entire device can be compromised.
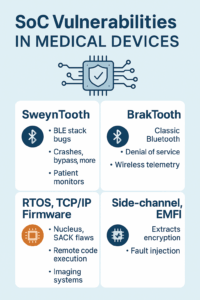
Key Vulnerabilities That Affect Medical Devices
1. SweynTooth (BLE Stack Vulnerabilities)
- A set of critical vulnerabilities found in Bluetooth Low Energy (BLE) stacks used by major SoC vendors like TI, NXP, Cypress.
- Allows attackers within radio range to crash, disable, or bypass authentication on BLE-enabled devices.
- Impacts: Patient monitors, wireless infusion devices, home health wearables.
2. BrakTooth (Classic Bluetooth Exploits)
- Affects SoCs using older Bluetooth implementations.
- Attackers can execute denial-of-service (DoS) attacks or run unauthorized commands remotely.
- Risks: Disruption of wireless telemetry or admin access without physical proximity.
3. NUCLEAUS:13 (TCP/IP Stack Exploits)
- 13 vulnerabilities in the Siemens Nucleus RTOS used in many SoCs.
- Enables remote code execution and system crashes—via malformed TCP/IP packets.
- Impacts: Imaging equipment, diagnostic interfaces, or devices using embedded web services.
4. EMFI and Side-Channel Attacks
- Electromagnetic fault injection (EMFI) or side-channel leakage can extract encryption keys or bypass secure boot on SoCs.
- May not require direct connection—only proximity and specialized gear.
Why This Matters for Medical Device Manufacturers
- SoCs are ubiquitous and often preloaded with vendor firmware and drivers.
- If unpatched or improperly configured, these components leave devices open to known exploits—even if your application software is secure.
- The FDA’s cybersecurity guidance and IMDRF premarket principles expect manufacturers to identify, assess, and document such risks.
In 2024, multiple healthcare systems experienced Bluetooth-based disruptions traced to unpatched SoC firmware—leading to urgent recalls and HHS alerts.
How to Mitigate SoC Risks
🔐 Technical Controls
- Secure Boot: Ensure firmware and OS cannot be modified without cryptographic validation.
- Firmware Validation: Validate all vendor libraries and BLE/TCP stacks via static and dynamic analysis.
- Anomaly Detection: Monitor for unusual wireless behavior (e.g., excessive BLE handshakes or packet sizes).
- Segmentation: Isolate high-risk interfaces on separate hardware or sandboxed memory.
🔄 Operational Best Practices
- Maintain an up-to-date Software Bill of Materials (SBOM) that includes SoC firmware, drivers, and libraries.
- Monitor CVEs and vendor advisories tied to your SoC’s BLE, RTOS, or connectivity firmware.
- Perform penetration testing and fuzzing focused on Bluetooth and TCP/IP stacks.
FDA Compliance Requirements
- Include SoC risks in your threat model and Secure Product Development Framework (SPDF)
- Justify patch strategy for vendor-provided binaries and drivers
- Provide firmware validation results in your eSTAR cybersecurity documentation
- Track SoC-related CVEs postmarket and update devices accordingly
Failure to address these risks could lead to:
- Delayed 510(k) or De Novo clearances
- Cybersecurity deficiencies in FDA responses
- Field recalls or patient safety alerts
FAQs
Q: If we don’t use wireless features, are SoC risks still relevant?
A: Yes. Many SoCs have Bluetooth or Wi-Fi modules embedded—even if unused. If not disabled properly, they may still be vulnerable.
Q: Should we test SoC components separately?
A: Absolutely. Fuzzing or pen-testing BLE, TCP/IP, and vendor libraries is critical—even if your application code is secure.
Q: How often should we check for SoC vulnerabilities?
A: Regularly. Subscribe to vendor advisories, monitor NIST NVD, and include SoC SBOMs in postmarket surveillance.
Final Thoughts
System on a Chip vulnerabilities are an increasingly urgent concern in medical device cybersecurity. These flaws impact not just software, but the core computing and communication fabric of your devices. By proactively identifying and addressing SoC risks, manufacturers can reduce regulatory delays, protect patients, and build more resilient products.
Need Help Validating Your SoC Attack Surface?
Blue Goat Cyber offers SoC-focused threat modeling, SBOM validation, and Bluetooth/TCP fuzz testing. We help you meet FDA expectations while uncovering hidden risks in vendor-supplied firmware.
👉 Schedule a consultation today to harden your devices—inside and out.
