Updated July 14, 2025
When designing medical devices, security and safety go hand in hand. One of the most overlooked but critical safeguards is input validation—the process of verifying, sanitizing, and controlling the data a device receives before acting on it.
From insulin pumps to hospital imaging systems, medical devices rely on a range of inputs: sensor data, user commands, network messages, or cloud instructions. If those inputs aren’t validated, devices become vulnerable to crashes, hijacking, or worse—unpredictable behavior that can compromise patient safety.
This article explains what input validation is, why it matters, and how to implement it in alignment with FDA cybersecurity guidance and the Secure Product Development Framework (SPDF).
What Is Input Validation?
Input validation is checking incoming data to ensure it meets predefined expectations. These checks can verify:
- Type (e.g., integer, string)
- Format (e.g., MM/DD/YYYY)
- Length (e.g., max 50 characters)
- Range (e.g., heart rate between 30–220 bpm)
- Sanitization (removal of special characters or harmful commands)
Why Input Validation Matters in Medical Devices
Unvalidated inputs are one of the leading causes of cybersecurity and functional failures in embedded systems. In medical devices, the stakes are higher:
- Patient harm: Malformed or spoofed inputs can trigger overdose, delay diagnostics, or crash devices.
- Data integrity loss: Invalid telemetry may corrupt patient logs or analytics.
- Regulatory risk: Failure to validate inputs can be cited in FDA deficiency letters or trigger recalls.
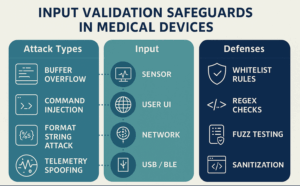
Common Attacks Prevented by Input Validation
| Attack Type | Description | Impact in Medical Devices |
|---|---|---|
| Buffer Overflow | Too much data crashes memory | Firmware failure, forced reboot |
| Command Injection | Malicious command via debug port or input | Unintended behavior, privilege escalation |
| SQL/XML Injection | Harmful queries through APIs or web forms | Data breaches, unauthorized access |
| XSS | Code injection into web-based UIs | Credential theft, interface hijacking |
| Telemetry Spoofing | False or altered input via BLE/sensors | Incorrect readings, misdiagnosis |
Best Practices for Input Validation
- Whitelist Input
Accept only known-good formats, ranges, or patterns. Avoid blacklists. - Sanitize Data at Entry
Remove special characters and escape sequences from input fields. - Validate Sensor & Wireless Input
Treat BLE packets, USB commands, and sensor signals as untrusted until validated. - Use Static & Dynamic Testing
Tools like fuzzers and static analyzers help catch unvalidated paths and edge cases. - Log Validation Failures
Log and analyze failed inputs to catch tampering or firmware bugs.
FDA Guidance: Validation Is a Must
The FDA’s 2025 Cybersecurity Guidance clearly expects input validation as part of a device’s SPDF and threat model.
“Software must verify that inputs are consistent with specifications and expected operating parameters. Failure to validate may result in software malfunctions or system compromise.” — FDA, 2025 Guidance
Document your validation routines in:
- eSTAR cybersecurity documentation
- Hazard analyses
- Software verification and testing plans
Real-World Example
A wearable glucose monitor accepted numeric values via BLE without range-checking. During a firmware test, a fuzzed signal set the blood sugar reading to 9999 mg/dL. This triggered an emergency insulin dose—thankfully in a test environment.
Fix: A simple range validation (50 ≤ value ≤ 400) would’ve prevented the event.
Final Thoughts
Input validation may sound like a developer detail—but for medical devices, it’s a core safety and security function. It protects patients, strengthens regulatory submissions, and forms the front line of cyber hygiene.
If your product processes commands, sensor input, or external data, make sure validation is built in, tested, and well-documented.
Partner With Blue Goat Cyber
We help medical device manufacturers build secure firmware, validate input channels, and align every control with FDA expectations. From testing to documentation, our team ensures your devices stay resilient—inside and out.
👉 Contact us to secure your device architecture and avoid input-driven risks.
